这篇指南将要向你介绍使用 Google Chrome 内建的开发者工具来调试扩展程序。
Chrome Extension:Debugging
This tutorial introduces you to using Google Chrome's built-in Developer Tools to interactively debug an extension.
View extension information
To follow this tutorial, you need the Hello World extension that was featured inGetting Started. In this section, you'll load the extension and take a look at its information in the Extensions page.
- Load the Hello World extension if it isn't already running. If the extension is running, you'll see the Hello World icon
 to the right of your browser's address bar.If the Hello World extension isn't already running, find the extension files and load them. If you don't have a handy copy of the files, extract them from this ZIP file. See Getting Started if you need instructions for loading the extension.
to the right of your browser's address bar.If the Hello World extension isn't already running, find the extension files and load them. If you don't have a handy copy of the files, extract them from this ZIP file. See Getting Started if you need instructions for loading the extension. - Go to the Extensions page (chrome://extensions), and make sure the page is in Developer mode.
- Look at the Hello World extension's information on that page. You can see details such as the extension's name, description, and ID.
Inspect the popup
As long as your browser is in Developer mode, it's easy to inspect popups.
- Go to the Extensions page (chrome://extensions), and make sure Developer mode is still enabled. The Extensions page doesn't need to be open for the following to work. The browser remembers the setting, even when the page isn't shown.
- Right-click the Hello World icon
 and choose the Inspect popup menu item. The popup appears, and a Developer Tools window like the following should display the code for popup.html.
and choose the Inspect popup menu item. The popup appears, and a Developer Tools window like the following should display the code for popup.html. The popup remains open as long as the Developer Tools window does.
The popup remains open as long as the Developer Tools window does. - If the Scripts button isn't already selected, click it.
- Click the console button
 (second from left, at the bottom of the Developer Tools window) so that you can see both the code and the console.
(second from left, at the bottom of the Developer Tools window) so that you can see both the code and the console.
Use the debugger
In this section, you'll follow the execution of the popup page as it adds images to itself.
-
- Set a breakpoint inside the image-adding loop by searching for the string img.src and clicking the number of the line where it occurs (for example, 37):
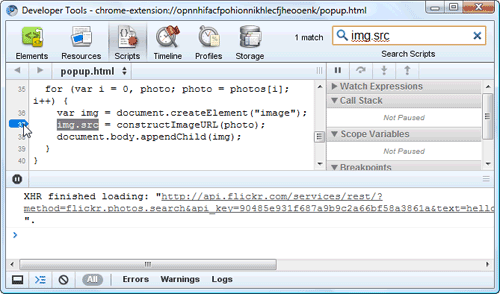
- Make sure you can see the popup.html tab. It should show 20 "hello world" images.
- At the console prompt, reload the popup page by entering location.reload(true):
1> location.reload(true)
The popup page goes blank as it begins to reload, and its execution stops at line 37. - In the upper right part of the tools window, you should see the local scope variables. This section shows the current values of all variables in the current scope. For example, in the following screenshot the value of
iis 0, andphotosis a node list that contains at least a few elements. (In fact, it contains 20 elements at indexes 0 through 19, each one representing a photo.)
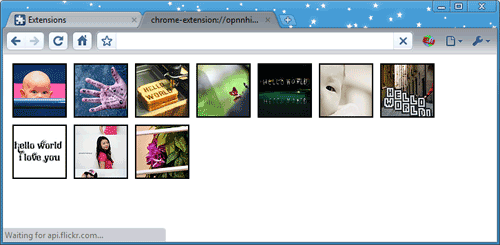
- Click the play/pause button
 (near the top right of the Developer Tools window) to go through the image-processing loop a single time. Each time you click that button, the value of
(near the top right of the Developer Tools window) to go through the image-processing loop a single time. Each time you click that button, the value of iincrements and another icon appears in the popup page. For example, wheniis 10, the popup page looks something like this:
- Set a breakpoint inside the image-adding loop by searching for the string img.src and clicking the number of the line where it occurs (for example, 37):
- Use the buttons next to the play/pause button to step over, into, and out of function calls. To let the page finish loading, click line 37 to disable the breakpoint, and then press play/pause
 to continue execution.
to continue execution.
Summary
This tutorial demonstrated some techniques you can use to debug your extensions:
- Find your extension's ID and links to its pages in the Extensions page (chrome://extensions).
- View hard-to-reach pages (and any other file in your extension) using chrome-extension://extensionId/filename.
- Use Developer Tools to inspect and step through a page's JavaScript code.
- Reload the currently inspected page from the console using location.reload(true).
Now what?
Now that you've been introduced to debugging, here are suggestions for what to do next:
- Watch the extensions video Developing and Debugging.
- Try installing and inspecting other extensions, such as the samples.
- Try using widely available debugging APIs such as
console.log()andconsole.error()in your extension's JavaScript code. Example:console.log("Hello, world!") - Follow the Developer Tools tutorial, explore the Developer Tools site, and watch some video tutorials.
For more ideas, see the Now what? section of Getting Started.
Content available under the CC-By 3.0 license
CMake如何编译CUDA(.cu)源文件
现在的项目,如果需要用到计算加速,Nvidia的CUDA往往是首选。那么如何在CMake中编译写好的CUDA源代码,可以参考如下。
首先使用FIND_PACKAGE找到已经安装的CUDA,此时需要配置的环境变量等,应该已经自动配置完成了
|
1 2 3 4 |
SET(CUDA_VERSION 8.0) FIND_PACKAGE(CUDA ${CUDA_VERSION} REQUIRED) STRING (TOLOWER ${CMAKE_SYSTEM_NAME} LOWER_SYSTEM_NAME) SET(CUDA_TARGET_INCLUDE ${CUDA_TOOLKIT_ROOT_DIR}-${CUDA_VERSION}/targets/${CMAKE_HOST_SYSTEM_PROCESSOR}-${LOWER_SYSTEM_NAME}/include) |
接下来,使用CUDA_ADD_LIBRARY取代原来的ADD_LIBRARY,如下:
|
1 2 3 4 5 6 7 8 |
CUDA_ADD_LIBRARY(mylib SHARED file1.cpp file2.cu file3.cpp OPTIONS -arch sm_20 ) TARGET_LINK_LIBRARIES(mylib ${CUDA_LIBRARIES}) |
如果是可执行程序,请使用CUDA_ADD_EXECUTABLE取代ADD_EXECUTABLE。
参考链接
Getting Started: Building a Chrome Extension
Extensions allow you to add functionality to Chrome without diving deeply into native code. You can create new extensions for Chrome with those core technologies that you're already familiar with from web development: HTML, CSS, and JavaScript. If you've ever built a web page, you should feel right at home with extensions pretty quickly; we'll put that to the test right now by walking through the construction of a simple extension that will allow the user to change the background color of the current webpage.
linux如何查看已加载的动态库
首先用ps命令找到进程的pid。
然后执行如下命令中的任意一个即可:
|
1 |
$ cat /proc/$PID/maps |
|
1 |
$ lsof -p $PID | grep .so |
|
1 |
$ pmap $PID |
参考链接
Chrome扩展:Manifest文件格式
任何扩展程序都有一个 JSON 格式的 manifest 文件,以 manifest.json 命名,记录了重要信息。
字段一览
下列代码展示了扩展程序支持的 manifest 字段,点击字段链接可以查看详情。
"manifest_version": 2,
"name": "My Extension",
"version": "versionString",// Recommended
"default_locale": "en",
"description": "A plain text description",
"icons": {...},// Pick one (or none)
"browser_action": {...},
"page_action": {...},// Optional
"author": ...,
"automation": ...,
"background": {
// Recommended
"persistent": false
},
"background_page": ...,
"chrome_settings_overrides": {...},
"chrome_ui_overrides": {
"bookmarks_ui": {
"remove_bookmark_shortcut": true,
"remove_button": true
}
},
"chrome_url_overrides": {...},
"commands": {...},
"content_capabilities": ...,
"content_scripts": [{...}],
"content_security_policy": "policyString",
"converted_from_user_script": ...,
"current_locale": ...,
"devtools_page": "devtools.html",
"event_rules": [{...}],
"externally_connectable": {
"matches": ["*://*.example.com/*"]
},
"file_browser_handlers": [...],
"file_system_provider_capabilities": {
"configurable": true,
"multiple_mounts": true,
"source": "network"
},
"homepage_url": "http://path/to/homepage",
"import": [{"id": "aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa"}],
"incognito": "spanning, split, or not_allowed",
"input_components": ...,
"key": "publicKey",
"minimum_chrome_version": "versionString",
"nacl_modules": [...],
"oauth2": ...,
"offline_enabled": true,
"omnibox": {
"keyword": "aString"
},
"optional_permissions": ["tabs"],
"options_page": "options.html",
"options_ui": {
"chrome_style": true,
"page": "options.html"
},
"permissions": ["tabs"],
"platforms": ...,
"plugins": [...],
"requirements": {...},
"sandbox": [...],
"short_name": "Short Name",
"signature": ...,
"spellcheck": ...,
"storage": {
"managed_schema": "schema.json"
},
"system_indicator": ...,
"tts_engine": {...},
"update_url": "http://path/to/updateInfo.xml",
"version_name": "aString",
"web_accessible_resources": [...]
}
Chrome扩展:构建一个 Chrome 扩展程序
扩展程序可以让我们不需要深入了解Chrome的原生代码就可以扩展Chrome浏览器的功能。 你可以用已经掌握的web开发核心技术HTML,CSS,和JavaScript来创建Chrome扩展程序。 如果你以前开发过网页,你可以很快地上手开发扩展程序; 接下来我们就马上开始,一步步地开发一个简单的扩展程序,这个扩展程序的作用是找出当前页面中所使用的谷歌服务器图片。
ubuntu 16.04.3上apache 2.4.18通过HTTP_REFERER阻止图片盗链
最近偶尔碰到网站的流量被消耗尽的情况,已经影响到自己的使用了。怀疑网站图片,数据等被盗链,导致流量被消耗。
ubuntu 16.04.3上apache 2.4.18防止网站图片被盗链的方法如下:
首先是在根目录下创建一个.htaccess,如果已经有了,直接把下面的代码添加到.htaccess尾部即可。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
#阻止盗链 <IfModule mod_rewrite.c> RewriteEngine on RewriteCond %{HTTP_REFERER} !^$ [NC] RewriteCond %{HTTP_REFERER} !google.com [NC] RewriteCond %{HTTP_REFERER} !baidu.com [NC] # 微软必应 RewriteCond %{HTTP_REFERER} !bing.com [NC] # 谷歌翻译 RewriteCond %{HTTP_REFERER} !translate.googleusercontent.com [NC] RewriteCond %{HTTP_REFERER} !mobibrw.com [NC] RewriteCond %{HTTP_REFERER} !miniab.com [NC] # 跳转到服务器首页 RewriteRule .*.(gif|jpg|png|zip|gz|tar|pdf)$ mobibrw.com [R,NC,L] # 服务器返回403禁止访问 # RewriteRule .*.(gif|jpg|png|zip|gz|tar|pdf)$ - [F] </IfModule> |
简单的解释下每条语句:
|
1 |
RewriteCond %{HTTP_REFERER} !^$ [NC] |
允许空“HTTP_REFERER”的访问,即允许用户在浏览器地址栏中直接输入图片地址时图片文件的显示。一般而言,这是可选的,不过,建议这么设置,如果强迫必须具有“HTTP_REFERER”才能访问,可能会带来某些问题,比如说在用户通过代理服务器访问时。
|
1 |
RewriteCond %{HTTP_REFERER} !google.com [NC] |
设置允许访问的HTTP来源,包括我们的站点自身、Google、Baidu等。这个可以添加多条,目前我们配置只有自身还有谷歌百度等常用的搜索引擎的访问权限。
|
1 |
RewriteRule .*.(gif|jpg|png|zip|gz|tar|pdf)$ mobibrw.com[R,NC,L] |
定义被盗链时替代的链接,可以是图片,也可以是404错误页,目前我们定义的是首页,所以就是mobibrw.com,如果是要定义在404页面,可以把404页面的路径加上。当然替换的页面文件体积越小越好。你也可以不设置替换图片,而是使用下面的语句即可(服务器返回403禁止访问):
|
1 |
RewriteRule .*\.(gif|jpg|png|zip|gz|tar|pdf)$ – [F] |
参考链接
ubuntu 16.04.3上apache2服务器报告错误“script not found or unable to stat: /usr/lib/cgi-bin/php*”
最近在查看服务器上的apache2的错误日志的时候,发现如下错误信息:
|
1 2 3 4 5 |
[Sun Jan 28 19:06:13.794012 2018] [cgi:error] [pid 3382:tid 139940209870592] [client 149.56.130.214:39 474] AH02811: script not found or unable to stat: /usr/lib/cgi-bin/php [Sun Jan 28 19:06:14.238284 2018] [cgi:error] [pid 3382:tid 139940117550848] [client 149.56.130.214:39 474] AH02811: script not found or unable to stat: /usr/lib/cgi-bin/php5 [Sun Jan 28 19:06:15.550249 2018] [cgi:error] [pid 3382:tid 139940226656000] [client 149.56.130.214:39 474] AH02811: script not found or unable to stat: /usr/lib/cgi-bin/php-cgi [Sun Jan 28 19:06:15.983952 2018] [cgi:error] [pid 3382:tid 139940125943552] [client 149.56.130.214:39 474] AH02811: script not found or unable to stat: /usr/lib/cgi-bin/php.cgi [Sun Jan 28 19:06:16.422075 2018] [cgi:error] [pid 3382:tid 139940033623808] [client 149.56.130.214:39 474] AH02811: script not found or unable to stat: /usr/lib/cgi-bin/php4 |
刚刚开始感觉莫名其妙,因为PHP的解析已经通过PHP-FPM模式进行处理,服务器上的配置已经不需要cgi进行处理了。
网上搜索了一下,发现这个是由于ubuntu上apache2的默认配置模版导致的,尤其是从ubuntu 12.04一路升级上来的系统,在配置模版中有指出/usr/lib/cgi-bin/这个路径,可是这个路径已经不再使用了。
修改方式如下:
|
1 |
$ sudo vim /etc/apache2/sites-enabled/000-default.conf |
向下查找,会发现如下内容:
|
1 2 3 4 5 6 7 |
ScriptAlias /cgi-bin/ /usr/lib/cgi-bin/ <Directory "/usr/lib/cgi-bin/"> AllowOverride None Options +ExecCGI -MultiViews +SymLinksIfOwnerMatch Order allow,deny Allow from all </Directory> |
如果确实网站已经不再使用任何cgi相关的东西了,可以直接注释掉这段代码。
另外如果开启了HTTPS,同理需要修改HTTPS对应的配置文件。
修改完成后,重启服务器:
|
1 |
$ sudo service apache2 restart |
参考链接
script not found or unable to stat: /usr/lib/cgi-bin/php-cgi
用Python在地图上模拟疫情扩散
最近在研究热力图,发现了一篇可能有用的Python模拟疫情扩散的文章,可以部分模拟热力图,整篇文章原文内容如下: